On December 8th, the Cybersecurity & Infrastructure Security Agency (CISA) released a great phishing infographic about data collected, lessons learned and recommendations learned from simulated phishing attacks that CISA has done for organizations. It is a great, independent, unbiased infographic with a lot of good data and recommendations. If you and your organization follow the included recommendations, you will be better off.
Each finding and recommendation is linked with specific Cybersecurity Performance Goals (CPGs) from CISA’s larger 2022 Cross-Sector Cybersecurity Performance Goals. So, it is great to be able to go from an infographic recommendation to a more formal recommendation and report, all created by the U.S. government’s largest agency dedicated to protecting people and organizations against cyberthreats.
Here are some of the key findings and some related sources for more information:
Most Successful Phishing Topics
CISA reported that three most successful simulated phishing topics were:
Financial-related security alerts or updates
Organizational announcement
User alerts and training updates
These are no surprises to people who follow the most popular phishing topics. KnowBe4 tracks the top, most frequently reported real-world and simulated phishing topics each quarter by our customers using our Phish Alert Button in our quarterly Top Clicked Phishing Email Subjects.
Every security awareness training program should do their best to educate and mimic the most likely threats. KnowBe4’s quarterly infographic gives you that information.
How Many People Will Click on a Phishing Email?
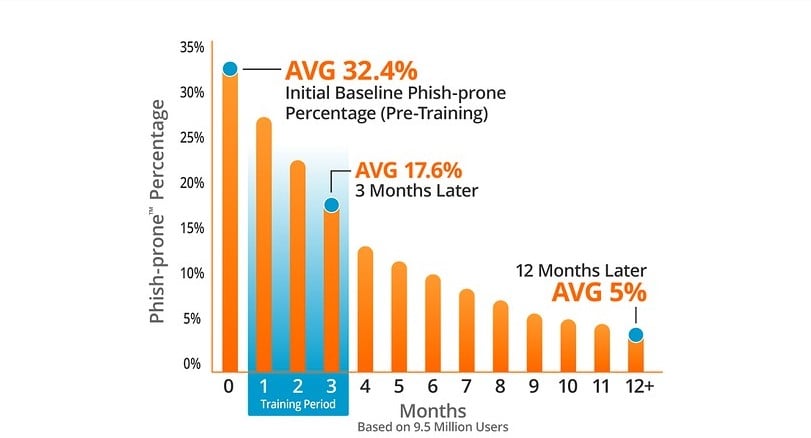
CISA reported that one out of every 10 people who got a simulated phishing test clicked on the included link or downloaded the attachment. CISA does not share what percentage of employees open the phishing test and did not take a required action. But KnowBe4’s long-time data, known as the KnowBe4 Phishing by Industry Benchmarking report has shown that in the average organization, just under one-third of employees will open and interact with a simulated phishing test.
Just under one-third of employees being “Phish-proneTM” is an average across all organizations and industries. We saw many industries with Phish-prone Percentage rates above 50% and the lowest rate we found across 9.5 million users was 20%. If the lowest rate is one-fifth of employees being tricked by phishing, it is clear that every organization needs to make sure their employees are educated about social engineering and phishing.
Our data shows that if organizations do the recommended simulated security awareness training and simulated phishing testing that our customers can get their Phish-prone rate down to 5% or less.
And since social engineering and phishing is the most common ways that hackers and their malware creations are successful, moving your Phish-prone rate from 32% to 5% or less is one of the best defenses any organization can do.
Malware Is Getting Through
CISA reported that 70% of malware or links to malware were not blocked by network border protection services and 15% of all malware was not blocked by endpoint detection products. That is very useful information. First of all, endpoint detection products appear to be far more accurate than network-based protection products. That one fact might surprise people. Second, a lot of malware and malicious links are getting past all the automated defenses and getting to the end user. It is clear that your end users will see phishing attempts and malware and will be your last line of defense. All employees need to be trained in how to recognize social engineering and what to do once they have detected it…which is hopefully reporting it to IT/IT Security.
Most Employees Do Not Report Attempted Phishing Events
Unfortunately, CISA reported that only 13% of targeted employees reported the phishing attempt. This is a huge problem and risk. As CISA stated in their infographic, failure by employees to report attempted phishing attacks can prevent IT/IT Security from determining if the phishing attack is an isolated event or a bigger campaign that needs immediate remediation.
Employees need to be taught how to recognize phishing attacks and how to appropriately report them. We are big believers in the easy-to-use, free Phish Alert Button. Appearing as a little icon on their email client task bar, it is easy to highlight a potential phishing email and with one click, make it both go away and also report it to IT/IT Security. If you make reporting phishing easy, your employees will be more likely to do it.
Phishing Quickness
CISA’s data says that 84% of employees [who] took the bait and interacted with the simulated phishing attempt, did so within 10 minutes. This means that defenders have a very limited time to both recognize that a phishing event has gotten past their defenses, remove the phishing attempt and use other mitigations to prevent its spread.
KnowBe4 highly recommends our PhishER product. With PhishER, users report suspected phishing attempts using our Phish Alert Button where the email can be analyzed and automatically be marked as an email threat (e.g., spam, phishing, etc.) and let administrators see if the newly submitted attack is part of a larger threat. If so, administrators can use PhishRIP to quickly remove all other copies that may have gotten to other users and use PhishFlip to turn real phishing emails into simulated phishing tests to quantify how many of your users would have fallen victim had the real phishing email gotten to them.
Automate Updates
CISA recommends that organizations update their software and firmware any time the vendor releases a critical security patch.
CISA Recommends DMARC
Every organization should enable DMARC, DKIM and SPF, the world’s three most common anti-phishing-domain-spoofing standards.
Everything You Can Do to Stop Phishing
It is clear from CISA’s phishing infographic that training your employees in how to recognize and report social engineering and phishing is one the best, if not the best, mitigations that any organization can to do best reduce cybersecurity risk.
Here is the bare minimum you need to teach every employee.
If you are interested in everything…every policy…every technical defense…every best practice education hint…we can think of to best mitigate social engineering and phishing, try KnowBe4’s free Comprehensive Anti-Phishing Guide.
CISA’s phishing infographic lays out the facts on social engineering and phishing. Phishing is one of the most likely ways that hackers and their malware creations can sneak into your environment. Many untrained employees will open any phishing email they receive, and many will click on the embedded links or download the attached malware. Network protection defenses are very unlikely to stop it and endpoint detection products are far from perfect. The single best mitigation that every organization could work on to improve is security awareness training for their employees.





